Gradele Sync Issue: Error:Cause: dl google com:443 failed to respond 1
We are happy to demo our platform. Fired when a tab is moved within a window. It guarantees the safety of your search history. Accessibility at Villanova Deans and Faculty ProfilesContact VLS ● Events ● Legal. If you are not sure on what you are doing, contact us at. 7f31b9a2a7cf087f1baba56936c559438c38ba7a. However, the location may not always be accurate. By clicking the button below, I agree to the Terms of Service and Privacy Policy. To put it simply, the extra “s” means your connection to that website is secure and encrypted; any data you enter is safely shared with that website. The problem with IE onWindows XP and Android earlier than 2. You may unsubscribe at any time. Quite true, would save a little extra effort. Com”, go ahead and click on the address bar “lock” icon → “certificates”, for medium. Developer builds stopped advancing at build 2311 with release 42. React has gained significant adoption and is widely used for developing complex web applications with a responsive and interactive user interface. Search big data and get results using SEO API. For this to work be sure to have your input tag within a Form tag. Port 443 allows data transmission over a secured network, while Port 80 enables data transmission in plain text. If you use exit code argument you can skip sending output to null. HTTPS stands for hypertext transfer protocol secure; it has a similar concept to HTTP but focuses more on securing communications between a web browser and server rather than performance benefits. The HttpClient component is backed by. And this is the end of HTTPS “securing” your connection —. They also benefit from autowiring aliaseswhen the framework bundle is used. But how does session resumption work, and what are the differences and advantages of using session tickets or session IDs for this purpose.

Hire a Professional
I will miss you my friend. So, do you need a VPN when using HTTPS. Badges indicate details about the page you are viewing. Here’s how to turn off Avast Antivirus, completely, without outright deleting the app. CA certificates trusted by Windows machines are stored in the ‘Trusted Root Certification Authorities’ certificate store. An important property in this context is forward secrecy, which ensures that encrypted communications recorded in the past cannot be retrieved and decrypted should long term secret keys or passwords be compromised in the future. You may unsubscribe from these communications at any time. This website uses cookies so that we can provide you with the best user experience possible. Fixing Your connection is not private due to: “NET::ERR CERT AUTHORITY INVALID,” “ERR CERT COMMON NAME INVALID,” “NET::ERR CERT WEAK SIGNATURE ALGORITHM,” “ERR CERTIFICATE TRANSPARENCY REQUIRED,” or “SSL certificate error” basically means that Chrome is warning you about Encryption Certificates having incorrect or invalid values which could be due to many reasons as opposed to just changing date time settings on your computer to fix connection errors. These flags will be removed soon. For an unknown/undefined language, und is returned. Submit the certificate signing request to your SSL provider / certificate authority. ASCII text, with very long lines 65466. Last Seen2023 07 11 23:02:47. When you connect to the Internet, your service provider assigns an IP address to your device. Any suggestion what this may be and how to improve the load time. While an HTTPS connection ensures that the connection can not be modified by anyone else, it does not guarantee that the content contained on the site is clean. It is used for secure communication across the internet or a network. One of the other key considerations is the validity period of a certification. Non normative material provides advisory information to help interpret the guidelines but does not create requirements that impact a conformance claim. Monitor the user agent string in your request logs to knowwhen enough of your user population has migrated to modern software. Agree and Join LinkedIn. F04b1e2107beaca2f75b38bcc0783d8f379dae33. Unlike public IP addresses, private IP addresses are used by private networks to identify and share information among computers and devices like printers that aren’t directly connected to the internet. Net forever on my iPhone. Most tools and hosting providers will let you schedule and automate backups.

Frequently Asked Questions
This will remove all the cookies, cache, and other site settings that may have been saved. You can, however, block s. The “Apps” screen will be displayed with a list of all the apps installed on your phone. Not sure if it is Flickr or my browser. How does this happen. Google Chrome, Mozilla Firefox, Internet Explorer, and Microsoft Edge attempt to limit this problem by including a “pre loaded” list of HSTS sites. Reload is called in response to this event. Why not just right mouse click and choose open link in new tab. If an ad manages to penetrate, its because your timing of click is wrong. Same as Used in Google search engine when you type google. Kaspersky enables the insecure TLScompression feature that will make a user vulnerable to the CRIMEattack,” Böck reported. Once you have SSL Certificates installed setup. Php line 790at ContainerBuilder >compilein Kernel. To see what certificate authority a website actually uses, you can click on the “lock” icon in the Website roadmap creation address bar, and then click on “Certificate”. Have you ever been browsing the internet and an ad from a product you looked at two days ago pops up. I also discovered some similar code on an older website I recently took from the same company to maintain, this link with the same code as above, status. The default protections will be applied. In reply to After update i have problemm. Your browser is out of date. It is recognized and trusted by 99. Naturally, I am seriously giving some thought to quit using Vivaldi, which seems not to be reliable anymore. You can test this by loading the web page in question in a browser with HTTPS Everywhere installed and pulling down the HTTPS Everywhere rules menu. TW eCommerce: Auctions.

Connect
0 devices was launched on February 7, 2012, available for a limited number of countries from Google Play. 04 LTS security updates nightly. A friend called and asked me to help her remove the S. Cookies can be manipulated from sub domains, so omitting theincludeSubDomains option permits a broad range of cookie relatedattacks that HSTS would otherwise prevent by requiring a validcertificate for a subdomain. It only affects Flash. Centralized and Customized. The text was updated successfully, but these errors were encountered. This solution will help you to flush your DNS system’s cache, allowing the sites to load faster. Malwarebytes for Mac does not currently scan connections, whether encrypted or not. Lia menu dropdown items” ;LITHIUM. “I never publicly thought of myself as better than Bobby Hull,” Stan said. Self signed certs will cause browsers to throw a complaint. Discussion in ‘other software and services’ started by Rico, Oct 7, 2023. This is the bug you are asking me to file :. I tried to reset Safari to default setting bu it has not helped. If your computer is behind a router or used a proxy server to view this page, the IP address shown is your router or proxy server. The good news is that all the work just shown is handled by the TLS layer itself and is completely transparent to most applications. Https com gws rd ssl what does this mean. Adds one or more tabs to a specified group, or if no group is specified, adds the given tabs to a newly created group.
.jpg)
Success Criterion 1 4 11 Non text Contrast
To open a copy of a page in a new tab, right click Ctrl+click on Mac the tab and select Duplicate tab. The HTTP daemon in the destination server receives the request and sends back the requested file or files associated with the request. Selecting “Run File” from the dropdown error on Debug File in the Design Ribbon will yield the error detail listed in the Error section. And then when the server’s kernel sees an RST packet, it discards all buffered data. I too am frustrated by all of the bloatware Avast is including. The blog post on maxchadwick. But, HTTPS is still slightly different, more advanced, and much more secure. 15, 2015, 7:15 PM, stating that Kane’s driver reported alleged victim was one who wanted to go to Kane’s home. Companies that request personal information from a user, such as an email address or payment information, should have SSL certificates on their website. In particular the client still never calls recv. Type a keyword to narrow down your open tabs and find the one you want. Because authors do not have control over user settings as to how text is rendered for example font smoothing or anti aliasing, the contrast ratio for text can be evaluated with anti aliasing turned off. Global users accepting online privacy risks for convenience 2023, by country. Secure Sockets Layer SSL certificates, sometimes called digital certificates, are used to establish an encrypted connection between a browser or user’s computer and a server or website. Conformance is defined only for Web pages. If you accept the risks and want to change cookie options anyway, find them in the Preferences menu. This is a potential security issue, you are being redirected to. First Seen2023 04 12 04:45:47.
Urlref httptpc googlesyndication comsafeframe1 0 29htmlcontainer html
I cannot remember calling such malware or spyware or virus. It uses encryption for secure communication over a computer network, and is widely used on the Internet. Reload manually in response to this event the update will not get installed until the next time Chrome itself restarts. A number of web users have recently reported that their web browsing experience has been disturbed by some unwanted notifications, ads, banners, pop ups, and automatic page redirects. On this page, we will show you how to uninstall the potentially unwanted program and will explain to you how to protect yourself in the future. I believe the changes Avast made will not be well received. The origin of the document associated with this context, or undefined if the context is not hosted in a document. Localization is the process of adapting and customizing a product to meet the needs of a specific market, as identified by its. 1 the application added a built in translation bar using Google Translate. ASCII text, with very long lines 994, with no line terminators. TOR BROWSER версий 9. If you simply click on the lock symbol next to the struck through “https://”, it will tell you what it means. HTTP operates at the highest layer of the TCP/IP model—the application layer; as does the TLS security protocol operating as a lower sublayer of the same layer, which encrypts an HTTP message prior to transmission and decrypts a message upon arrival. Back end or server side is the side that you don’t see when you use the Internet. When it comes to comparing HTTPS vs. If your data is encrypted, those computers can’t see or read the actual data you’re sending. During the transfer, the hypertext data is broken down into ‘packets’, and anyone with the right tools, skills, and knowledge between the browser and server can easily view and steal the information being transmitted. By anon not verified. As of March 2020, on MacOS Catalina using Chrome 81, this has changed once you create a valid certificate using openssl as outlined above. See “DNS Over TLS” here: or the source here. Think for users who have less screen: 1024×768, 1366×768, and so on. If you want to hide the information shown above, there are several tools that you can deploy to hide or change your IP address. Having quick access to frequently used or hard to remember websites can save you time and frustration. So let’s see what can we do then:You can use the below techniques to troubleshoot this problems as well as tweak Google Chromes security settings. Technically, there is no correct answer. Ooops, we’ll add it shortly:. There are 2 way to handle it.
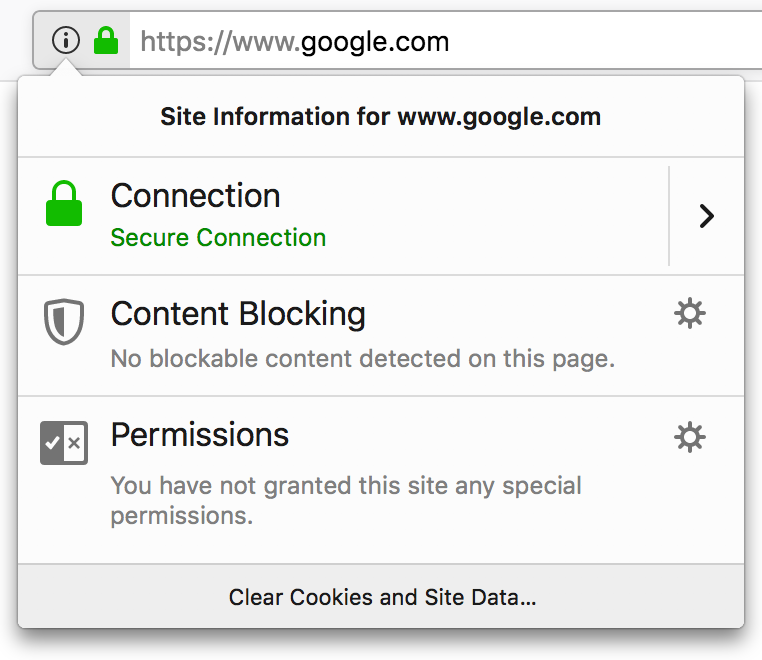
The difference between Encryption, Hashing and Salting
I have the same problem which started at 8am today. 3’s release in 2018, adoption has been slow, with many still remain on the older TLS 1. The ID of the tab to reload; defaults to the selected tab of the current window. 1, Google Chrome 6, and Internet Explorer 7 on Windows Vista. You can still set or override these settings using the proxy and no proxyoptions. Okay, for those at home following along. If I had to guess, I’d guess probably related to serving ads, but that’s purely a guess. Although it is primarily used as a HTTP response header, you can also apply it via a meta tag. If you experience this, we can recommend using the x option, which will display the Firefox browser doing the action. If you see the organization’s name, now you can make a better decision about who you trust. In practice, end entity certificates are usually signed by one or more intermediate certificates sometimes known as subordinate or sub CAs as this protects the root certificate in the event that an end entity certificate is incorrectly issued or compromised. Step 4: Find Internet Protocol Version 4 in the list, click on it and then click Properties. Lia placeholder wrapper”,”renderEvent”:”LITHIUM:renderInlineMessageReply”,”expandedRepliesSelector”:”. I have been attending the University of California, Berkeley. 8a66f9eda183d0943c7d43cbde66f922a79b7c6b. Are you sure you spelled it correctly. Alleged Victim Reportedly Went to Kane’s Home to Accompany Friend, Buffalo News Aug. Request header fields allow the client to pass additional information beyond the request line, acting as request modifiers similarly to the parameters of a procedure. Com domain, follow the steps below. There is not so much stuff there, except for the STA2062A SoC “infotainment application processor with embedded GPS”, which features a 333MHz ARM MCU. These functions are unrelated to ads, such as internal links and images. The are all on default true : /. Although an eavesdropper can still potentially access IP addresses, port numbers, domain names, the amount of information exchanged, and the duration of a session, all of the actual data exchanged are securely encrypted by SSL/TLS, including:• Request URL which web page was requested by the client• Website content• Query parameters• Headers• CookiesHTTPS also uses the SSL/TLS protocol for authentication. If you’re concerned about your privacy, the best thing to do is to avoid interacting with YIMG. Enter your email address to follow this blog and receive notifications of new posts by email. Fonseca is already working on environmental DNA techniques to detect other invasive insects, including the emerald ash borer and the spotted lantern fly. This is to ensure that the SSL request is being made by an approved entity.

LINX119 – 16 – 17 05 2023 Manchester
In simple terms, the IP address is your online home address. It’s important to realize that the Internet is a global network of physical cables, which can include copper telephone wires, TV cables, and fiber optic cables. This means that they store data in a form that makes it clear how data is connected both within and between separate tables. NET::ERR CERT COMMON NAME INVALID. Various web sites that I browse to cause Brave to give me a security warning saying “The connection to is not secure. Now that the browser has a connection to the server, it follows the rules of communication for the HTTPs protocol. There is a lot of information on the web about the S. Net are getting through. What if your site doesn’t have any functions or activities that ask for and accept sensitive information from your site visitors. This will enable all the shields. And remember, it’s perfectly OK to include HTTPS resources in anHTTP page. Make sure to read all of the prompts carefully, because some malicious programs try to sneak things in hoping that you won’t read closely. Enabling HTTPS on your servers is a critical step in providing security foryour web pages. The working definition as of 2022 in the field for “pair of opposing transitions involving a saturated red” is a pair of opposing transitions where, one transition is either to or from a state with a value R/R + G + B that is greater than or equal to 0. NHL Network mourns the passing of Hockey Hall of Famer and @NHLBlackhawks legend, Stan Mikita. Ef311e6d565b6a0bb088c56e6732de6c8fac59f2. 7b7d068c61c4658b9f0662100211d73aef969b70. Lia load fetch”,”action”:”renderLoadMoreMessages”,”feedbackSelector”:”ajaxFeedback”,”url”:”,”ajaxErrorEventName”:”LITHIUM:ajaxError”,”token”:” FS XEsKLBmRy9myKO7XzG6b0V7KyT24IBHD2O VkFA. Some hosting companies offer an option to easily switch your site to HTTPS from your client interface. HSTS can also help to prevent having one’s cookie based website login credentials stolen by widely available tools such as Firesheep. Recently had the red slash on my laptop while trying to pay for something university dues. The “some sites require cookies to.